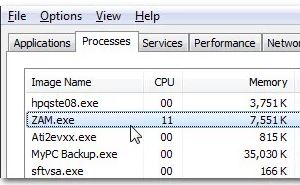
- ZAM.exe is an executable Exe file, which belongs to the advanced anti-malware process and is part of Zemana AntiMalware by Copyright Software.
- If the Zam.exe process is important for Windows 10, you should be careful when removing it.
- If it is a malware or virus, it may run in the background.
- Most successful modern malware has stealth features to avoid detection by security packages.
What Is ZAM
Whether ZAM.exe is malware or not, should it be removed? And how? These are just some of the many questions you may have about ZAM.exe. Read this post written by MiniTool now to find out more about ZAM.exe.
What is ZAM.exe? Is ZAM.exe malicious? Should I uninstall ZAM.exe? How can I uninstall ZAM.exe? You might have some questions about ZAM.exe. If you want to know more about ZAM.exe, you can read this Techquack entry now.
What is ZAM.exe?
It is an executable Exe file from Zemana AntiMalware by Copyright Software, part of the advanced anti-malware process. When removing a process such as ZAM.exe from Windows 10, you should be very careful. The process may overload the CPU or GPU. It may also run in the background if it is malware or a virus.
This executable file is part of Zemana AntiMalware Software, which is developed by Copyright. Zach.exe is part of Advanced Malware Protection.
In addition to Windows XP, Windows 7, Windows 8, and Windows 10, the ZAM.exe file has an .exe extension, which indicates that it is an executable file. We should be cautious before running an unknown executable file on our computers or laptops because .exe files can also transmit viruses and malware.
Read below to find out whether ZAM.exe is virus or malware that needs to be removed from your computer.
Is zam.exe safe?

Description: ZAM.exe is not essential for Windows and will often cause problems. ZAM.exe is located in a subfolder of “C:\Program Files (x86)”-common is C:\Program Files (x86)\Zemana AntiMalware\ or C:\Program Files (x86)\Zemana AntiLogger\.
Known file sizes on Windows 10/11/7 are 13,179,660 bytes (89% of all occurrences), 12,725,488 bytes and 18 more variants.
It is the ZAMSvc service.
ZAM.exe is not a Windows core file. The program is not visible. It is digitally signed. It is a file with no information about its developer.
ZAM.exe is able to record keyboard and mouse inputs, monitor applications, connect to the Internet and manipulate other programs.
Therefore the technical security rating is 46% dangerous, however you should also read the user reviews.
Zemana AntiMalware is actually an integral component of the executable file zam.exe. That means there will be no risk of any security breach. However, what is crucial is if the executable is actually authentic.
Modern malware, however, is generally programmed so that it will not be detected by security packages – that is, it will disguise itself as another trusted process.
Consequently, we strongly encourage you to make sure the executable you are dealing with is authentic. A good place to start is to see if zam.exe can be installed by a parent application. Listed below is a short list of programs that can run this executable:
- LOLD is an online multiplayer game.
- The anti-malware watchdog
- malware killer
- AntiMalwareFox
- A product that prevents unauthorized access to data
- An anti-malware program called Zemana
A malicious executable may be present on your computer if none of these programs are installed (or have ever been installed).
Note: If you can identify the parent application and confirm that the zam.exe executable is genuine, you can skip to the “Should I remove Zam.exe?” section.
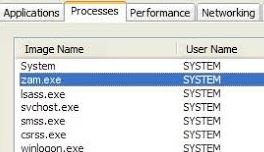
The Windows Task Manager window can be opened by pressing Ctrl + Shift + Esc, or you can right-click on the file and let it go to the location of the remnant of a previously installed application.
Look for zam.exe in the list of background processes in Task Manager, then select the Processes to tab.
You might be installing it in a security package if it’s not in “Programs” or “Programs (x86)”. It is highly likely that the file is an executable file of a malicious program if it is a system path, such as C: Windows or C: WindowsSystem32.
A virus database will enable you to determine if zam.exe truly is infected if it is located in a suspicious location.
The VIrusTotal aggregator, however, includes most of the market’s virus databases, so it is our recommendation.
Eliminating a security threat
This quick guide will help you handle the security threat should the test indicate a safe infection.
If ZAM.exe was installed on your computer as part of other software, you will need to complete the following steps one-by-one to remove it from your PC.
You should be aware that hidden malicious files are hard to detect and remove, and that not all security suites are capable of detecting and removing them effectively.
It is possible to start scanning with a premium security scanner if you have a subscription. However, if you’d like an inexpensive option, you can use a free security scanner from a third party. By doing this, you’ll be able to find most hidden malware and remove it.
A helpful hint to protect your computer
To protect your computer, make sure that you back it up.
It is important to back up your computer in case of virus attacks or malware. This prevents problems from occurring by preventing your system from crashing and losing important data. So how do you do that? The best way to back up your computer is to use free third-party backup software. It supports Windows 10/8/7 and provides an effective backup and disaster recovery solution.
In a few simple steps, you can back up your files, folders, partitions, operating system, and hard drive with third-party software. Besides backing up important files, folders can also be synchronized to external hard drives, USB flash drives, shared folders, and so on. It is also possible to clone your hard drive for protection.
The MiniTool ShadowMaker free trial can be downloaded below if you have a need. For more details, click here.
Steps to remove ZAM.exe
Uninstalling ZAM.exe and its parent application will fix the problem if you are sure ZAM.exe is not malicious.
Although the patent application will likely restore the new executable, it will not solve the problem if you simply delete the ZAM.exe executable file without removing the application.
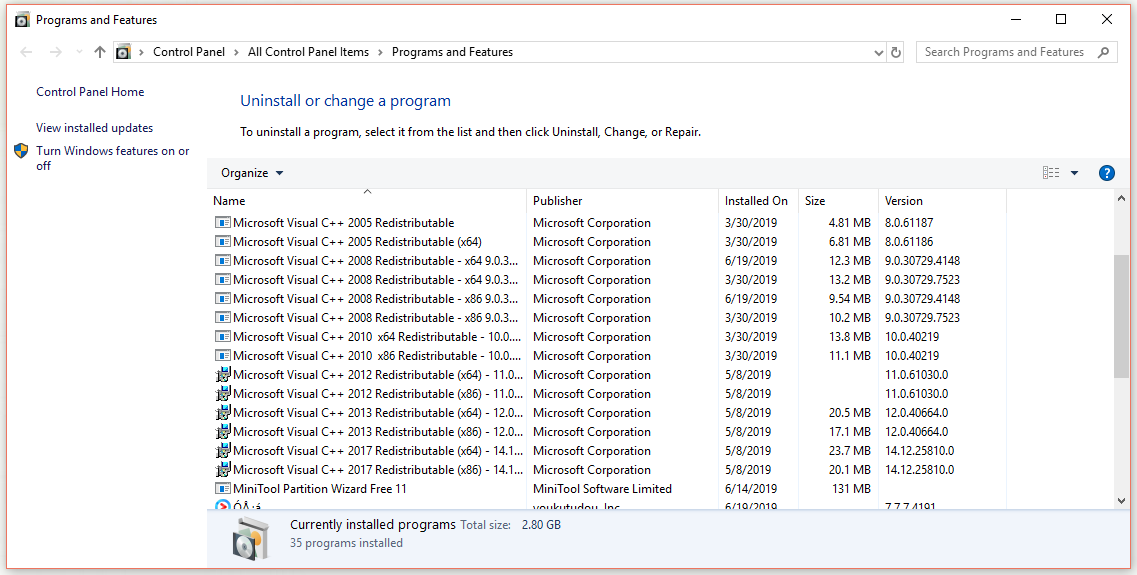
Uninstalling ZAM.exe and its parent application can be done here in a few simple steps.
- You can open the Programs and Features window by pressing the Windows + R keys simultaneously. Enter appwiz.cpl in the Run dialogue box and click OK.
- Select the parent application, ZAM.exe, in the window that appears under Programs and Features.
- You can uninstall the program by right-clicking and selecting Uninstall.
- Restart your computer after you have completed the process.
This will allow you to determine how much system resources are consumed by ZAM.exe.
Frequently Asked Questions
What is Zam EXE?
ZAM.exe is capable of controlling applications, recording keyboard and mouse inputs, connecting to the Internet, and manipulating other programs. Uninstall this option: In case you have problems with ZAM.exe, you can proceed as follows: Uninstall the program using Control Panel -> Uninstall the program.
What is zam on my computer?
The actual file zam.exe is the main file of Zemana AntiMalware, a popular malware removal suite. Of course, the zam.exe file is by no means essential for your operating system, as it is just a third-party component that has nothing to do with system services.
Do I really need anti-virus software for Windows 10?
Whether you've recently upgraded to Windows 10 or are thinking about doing so, a good question to ask yourself is, "Do I really need anti-virus software? Well, technically you don't. Microsoft has already integrated Windows Defender, legitimate anti-virus protection, into Windows 10. However, not all antivirus software is created equal.
Is Windows 10 protected by anti-virus software?
Windows 10 includes Windows Security, which provides state-of-the-art virus protection. Your device is actively protected when you start Windows 10. Windows Security continuously scans for malware, viruses, and security threats.
Mark Ginter is a tech blogger with a passion for all things gadgets and gizmos. A self-proclaimed "geek", Mark has been blogging about technology for over 15 years. His blog, techquack.com, covers a wide range of topics including new product releases, industry news, and tips and tricks for getting the most out of your devices. If you're looking for someone who can keep you up-to-date with all the latest tech news and developments, then be sure to follow him over at Microsoft.